Deliverability
Email spoofing: How brand impersonation really works
Email spoofing is no joke. Find out how scammers impersonate your company in the inbox and learn how to protect your subscribers as well as brand reputation.

PUBLISHED ON
Celebrity impressions are hilarious. Who doesn’t love a good Sean Connery or Marlon Brando impersonation? But when bad actors impersonate your brand through email spoofing, it’s no laughing matter.
Because email is such a personal and trusted communication channel, it also tends to be the preferred playground for cybercriminals. It’s estimated that 91% of cyberattacks start with email phishing. Global cybercrime cost the world $6.9 billion last year. Thankfully, there are some steps your brand can take to protect people from these bullies.
No one knows how to stop the bad guys like the team at Sinch Email who protects the Mailgun and Sinch Mailjet platforms. Mailgun has released an email security and compliance guide to help senders understand how to take on challenges like email spoofing.
We used some of those insights to create an infographic, which explains exactly how bad actors are able to impersonate your brand through a fake email message with malicious links. Plus, we’ve also got some advice on how to identify these phishing attempts and stop email spoofing from ever reaching the inbox.
Table of content
How email spoofing works
1. Use strong email authentication
2. Protect and update SMTP credentials and API keys
3. Use multifactor authentication
4. Educate employees and subscribers about the risks
Anatomy of an email spoofing scam
Ever wondered how email spoofing actually works? Check out how bad actors use brands to abuse the inbox in this infographic.
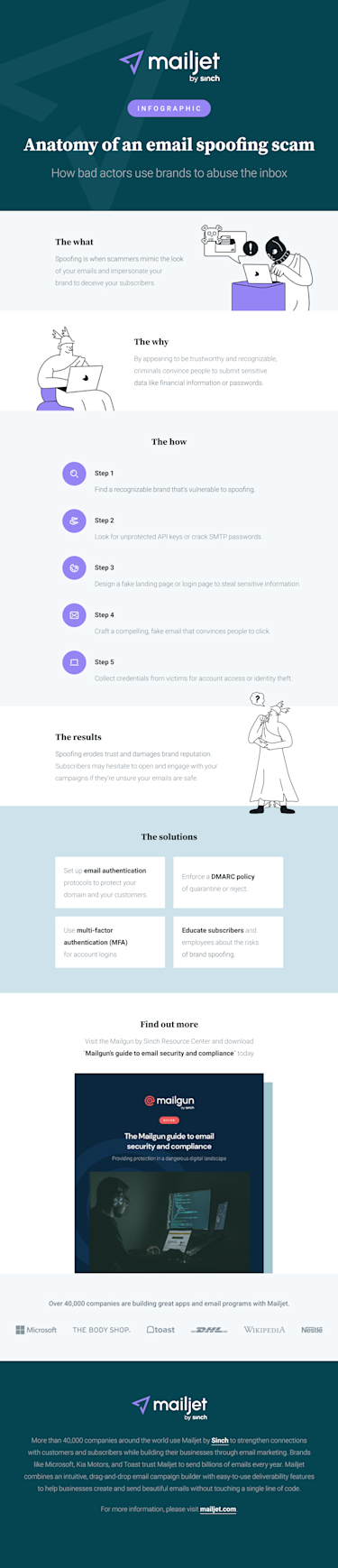
Click to view a larger graphic
What is email spoofing and brand impersonation?
Email spoofing is a form of phishing in which scammers send fraudulent emails designed to look like they came from a trustworthy, recognizable brand. The goal is to collect account credentials, financial information, or other data that lets cybercriminals carry out dirty deeds like identity theft. A spoofed email could also contain malware or ransomware that gets installed on the victim’s device.
You may hear the term “domain spoofing” used in a similar context. That’s because bad actors impersonate sending domains and websites.
How email spoofing works
After receiving a malicious email, recipients are urged to click a link that takes them to a webpage, which is also designed to look like the real thing. These fake webpages are often very convincing login pages where unsuspecting victims enter account credentials. Bad actors may also persuade people to reveal other sensitive data such as bank account information or credit card numbers.
Here’s a fake PayPal login page. It’s probably hard to tell the difference between the design of the phishing website and PayPal’s real login page. But take a closer look at the URL in the address bar. That’s a little fishy (or phishy) with those double dashes. Yet it could be easy to miss.

Fake PayPal login page for brand spoofing
All a scammer needs are some basic design tools and your logo. Then it’s awfully easy to spoof your brand and fool your customers or employees. Yes, you should be concerned about spoofing�’s negative impact inside your organization too.
Mailgun was able to thwart an SMS phishing attack, which attempted to spoof a brand that provides a service that everyone in the company uses. Unfortunately, other organizations aren’t always as vigilant about cybersecurity.
Many times, an email spoof will contain a sender name or domain name that is close to but not quite the same as your brand’s. For example, it may include hyphens in places where they wouldn’t normally be (mail-jet.com).
However, if a cybercriminal is able to hack SMTP passwords or access your secret API keys, they can literally send as your brand. In this case, they’ve essentially hijacked your email program. And that could be a major disaster.
Which brands are most likely to get spoofed?
Scammers do have some favorite targets for brand impersonation. Microsoft and LinkedIn top the list of most spoofed brands. Fintech companies and financial institutions in general are frequently spoofed. The same goes for ecommerce companies like Amazon as well as shipping and logistics companies like DHL. Social media and software as a service (SaaS) brands are also phishing favorites.
There’s one thing these different types of brands have in common: They all send a lot of transactional emails. That includes order confirmations, password resets, billing, and account creation emails. These kinds of communications are often used in spoofing because they deal with the kinds of sensitive information bad actors want.

An example of Amazon brand spoofing
There are a few telltale signs of phishing in the fake Amazon email:
Sender name: “Amazon Head Office” sounds totally made-up.
Sender address: It’s not even related to the brand.
Subject line: The scammer tried to use the brand/sender’s name here instead, which isn’t normal.
Sense of urgency: Presenting a problem that needs to be fixed is a common way to get people to click. Ironically, fraudsters use fake fraud alerts often.
Link text: It says amazon.com, but that’s not where it will take you.
This Amazon brand impersonation attempt counts on the possibility that the recipient has an active Amazon order. Of course, a lot of people will be waiting for an order. To hit a payday, all scammers need is one person to fall for the spoof.
Of course, you don’t have to be a Fortune 500 company to become the target of brand spoofing. Security experts say that smaller brands are vulnerable because they are less likely to have the right email authentication protocols in place.
We’re not immune either. Scammers have even tried spoofing Mailjet in an attempt to fool our customers.

As you can see, this phishing attempt aimed to get people to enter credit card information. When we found out about this, we quickly took steps to alert and educate our subscribers about the threat.
How to stop email spoofing
There is some good news. Thankfully, there are ways to fight back against bad actors trying to impersonate your brand. Here are some of the tips you’ll find in Mailgun’s email security guide:
1. Use strong email authentication
Email authentication helps mailbox providers like Gmail, Outlook, and Apple Mail identify fraudulent emails and decide what to do with them.
This means using SPF (Sender Policy Framework) and setting up DKIM (Domain-keys Identified Mail). But the best way to stop email spoofing is to use DMARC (Domain-based Message Authentication, Reporting, and Conformance) with a policy set to either quarantine or reject.
If you plan to start using Mailjet as your new ESP, you’ll find information on setting up authentication in our help center.
2. Protect and update SMTP credentials and API keys
If bad actors can crack SMTP passwords or gain access to your API keys, then even email authentication won’t stop spoofing. That’s because they’ll be able to send as your domain.
Protecting SMTP credentials and API keys should be a top priority for email security. Update them regularly and never share them. Mailjet users can find out how to update API keys here.
3. Use multifactor authentication
Multifactor authentication (MFA) provides an additional layer of security. If your customers log in to access their accounts or use your application, multifactor or two-factor authentication (2FA) helps mitigate the impact of phishing emails. This way, even if a bad actor obtains account credentials, they can’t get in without access to the user’s mobile device or email.
To protect employees, consider implementing Single Sign-on (SSO) or Security Assertion Markup Language (SAML) as a company-wide security solution.
4. Educate employees and subscribers about the risks
Many organizations have annual email security training for all employees. However, teaching your customers about email spoofing can help keep them safe while protecting your brand’s reputation.
If there’s certain information your company never asks for via email communication, make sure your subscribers know that. If you learn about phishing attempts that impersonate your brand, tell your customers about them.
The security experts at Mailgun say being proactive is a good idea. But if you do get spoofed, you should use it as an opportunity to maintain and regain trust in your brand.
“The last thing you want is for your company to be named in an email that looks legitimate, but it puts the recipient in a bad spot. I think that’s something senders often realize after it’s too late. Then they need to backtrack. So, if you get spoofed, be transparent. Communication is key. Tell people what happened and what you’re doing to shore things up, so it doesn’t happen again.”
Jonathan Torres, TAM Team Manager at Sinch Mailgun
Why you can trust us with email security and compliance
Mailjet and Sinch Mailgun are committed to providing our customers with best-in-class security. We’re also serious about data privacy, including strict adherence to GDPR compliance. That’s why we have ISO certification and SOC 2 Type II security audits for both brands.
The bottom line? This means you can send from our platforms knowing that we’re working to protect your privacy as well as the people on your email lists.
Find out more about what makes Mailjet a secure email solution as well as how Mailjet protects your data.
Free guide
Expert advice on email security and compliance
The team at Sinch Mailgun has all the answers you need to improve email security. That includes email authentication setup, GDPR compliance, and ways to protect employees and customers from phishing. Get “The Mailgun guide to email security and compliance” to find out more.








